
A global digital enterprise, operating in a highly regulated sector, relied on AWS-based, cloud-native platforms to serve millions of customers. With mission-critical applications and strict regulatory demands, the business required maximum uptime, operational agility, and robust compliance.
Before: Disconnected monitoring, heavy manual intervention, and slow incident escalations.
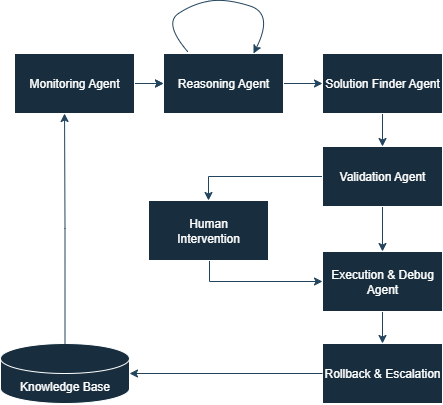
After: Integrated observability, AI-powered automation, and seamless human oversight for critical scenarios.
Agile Delivery Model: Focused sprints enabled iterative agent integration, process alignment, and quick wins.
Measurable Outcomes:
| Layer | Technology Stack |
| LLM Platform | Amazon Bedrock |
| Embedding Models | Bedrock Embedding Models |
| Orchestration | n8n |
| Monitoring | AWS CloudWatch, Prometheus, Grafana |
| Vector Database | Qdrant |
| External Search | Tavily API, Serp API |
| Security & Compliance | AWS IAM, TLS 1.2/1.3 |
CI/CD pipelines for automated, dependable deployments.
Real-time audit logging for complete traceability.
Custom API integrations expanding automation to custom and legacy components.
CloudifyOps Pvt Ltd, Ground Floor, Block C, DSR Techno Cube, Survey No.68, Varthur Rd, Thubarahalli, Bengaluru, Karnataka 560066
CloudifyOps Pvt Ltd, Cove Offices OMR, 10th Floor, Prince Infocity 1, Old Mahabalipuram Road, 50,1st Street, Kandhanchavadi, Perungudi, Chennai, Tamil Nadu - 600096
CloudifyOps Inc.,
200, Continental Dr Suite 401,
Newark, Delaware 19713,
United States of America
Copyright 2025 CloudifyOps. All Rights Reserved
