This is the second of the two part blog on managing secrets in Kubernetes with Vault. In this blog, we explore dynamic secrets.
Secrets require regular updates for enhanced security. For instance, passwords should be periodically changed, but how does your application detect these changes? While Kubernetes refreshes secrets, it lacks a built-in mechanism to notify applications of updates. Some manual approaches, such as checksums or restarting Pods, can be implemented, but they are often impractical in high-availability environments.
This is where cloud management services play a crucial role by integrating a dynamic secret engine to automate secret rotation. With automated secret management, applications can securely update credentials without downtime, ensuring seamless operations while maintaining strong security policies. By leveraging cloud management services, businesses can enhance security, streamline secret handling, and improve overall infrastructure resilience.
A cloud consulting company can leverage Vault’s database secrets engine to enhance security and compliance by dynamically generating database credentials based on user-defined roles. This ensures that each application or user receives temporary, least-privilege access to the database, reducing the risk of credential exposure. Additionally, database administrators can predefine the time-to-live (TTL) for these credentials, ensuring automatic revocation upon expiration or when they are no longer needed. This approach strengthens security, minimizes the risk of credential misuse, and simplifies access management in cloud environments
docker run -d
-p 0.0.0.0:27017:27017 -p 0.0.0.0:28017:28017
–name=mongodb
-e MONGO_INITDB_ROOT_USERNAME=”mdbadmin”
-e MONGO_INITDB_ROOT_PASSWORD=”hQ97T9JJKZoqnFn2NXE”
mongo
Login inside Vault server with root
Give root token from cluster master key file.
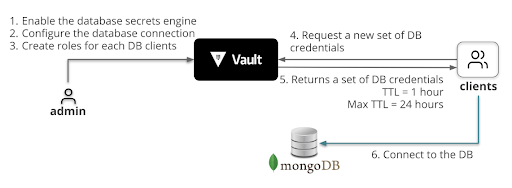
We will configure the MongoDB secrets engine and create a “tester” role with read and write permissions.
The database secrets engine is enabled at mongodb/.
The database secrets engine supports many databases through a plugin interface. To use a MongoDB database with the secrets engine requires further configuration with the mongodb-database-plugin plugin and connection information.
vault write mongodb/config/mongo-test
plugin_name=mongodb-database-plugin
allowed_roles=”tester” connection_url=”mongodb://{{username}}:{{password}}@127.0.0.1:27017/admin?tls=false”
username=”mdbadmin”
password=”hQ97T9JJKZoqnFn2NXE”
A role is a logical name within Vault that maps to database credentials. In this step, we are creating a “tester” role with TTL set to 1 hour, and the maximum TTL is 24 hours. This allows Vault to revoke the credentials automatically once they reach the TTL.
Create the role named tester.
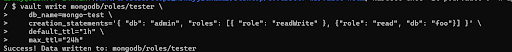
Verify that the tester role exists.
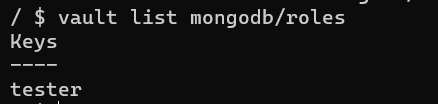
To connect to the MongoDB, Vault clients request Vault to dynamically generate the database credentials based on its role, in this case, the tester role.
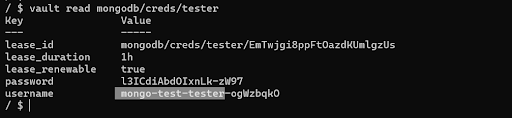
Read credentials from the tester database role.
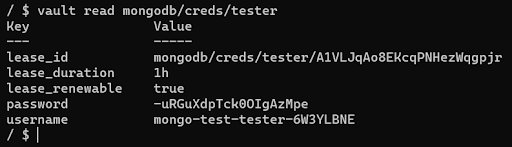
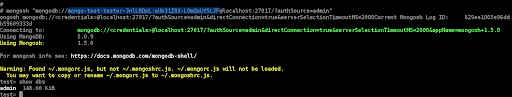
We can validate this by logging into mongodb with these credentials for the admin database.
Validation
mongodb://mongo-test-tester-6W3YLBNE:-uRGuXdpTck0OIgAzMpe@localhost:27017/?authSource=admin
Create a clients policy.
vault policy write clients –<
# Required: Get credentials from the database secrets engine for ‘tester’ role.
path “mongodb/creds/tester” {
capabilities = [ “read”, “update”]
}
Create a token with the clients policy attached.
Update the mongo-test connection configuration to specify that the generated database username should have the format of mongo-
vault write mongodb/config/mongo-test
plugin_name=mongodb-database-plugin
allowed_roles=”tester” connection_url=”mongodb://{{username}}:{{password}}@13.127.237.6:27017/admin?tls=false”
username=”mdbadmin”
password=”hQ97T9JJKZoqnFn2NXE”
username_template=”mongo-test-{{.RoleName}}-{{random 8}}”
The username_template parameter specifies the username format (“mongo-test-{{.RoleName}}-{{random 8}}”). The {{.RoleName}} returns the role name (tester) used to request a lease. The {{random 8}} returns 8 random characters.
Request a new set of credentials.
Follow us on our LinkedIn Page. To know more about our services, visit our website.
CloudifyOps Pvt Ltd, Ground Floor, Block C, DSR Techno Cube, Survey No.68, Varthur Rd, Thubarahalli, Bengaluru, Karnataka 560066
CloudifyOps Pvt Ltd, Cove Offices OMR, 10th Floor, Prince Infocity 1, Old Mahabalipuram Road, 50,1st Street, Kandhanchavadi, Perungudi, Chennai, Tamil Nadu - 600096
CloudifyOps Inc.,
200, Continental Dr Suite 401,
Newark, Delaware 19713,
United States of America
Copyright 2025 CloudifyOps. All Rights Reserved
