In our previous blogs we discussed how to create and optimize SIEM and case management systems for SOC. Both these systems need to be integrated via an automation platform for an efficient SOC.
As cyber threats become more sophisticated, Security Operations Centers (SOCs) need robust solutions to stay ahead. A Security Orchestration, Automation, and Response (SOAR) platform provides a centralized approach to managing and responding to threats efficiently. Among the many options, Shuffle stands out by offering customizable workflows, seamless integration with various security tools, and intelligent automation features. In this blog, we’ll guide you through setting up a SOAR platform for your SOC—while highlighting the role of Cloud Consulting Services and Cloud Security Services in strengthening your security posture.

Shuffle is a SOAR platform that allows you to collect, enrich, automate, and respond to security events with little to no human interaction required. Workflows are the part of Shuffle where everything comes together. Using Apps, Triggers, and Variables, Shuffle gives you access to all the tools you need to make your platforms talk to each other.
We deployed Shuffle as a cluster setup with EFS (Elastic File System) to ensure data persistence and Multi-AZ availability, allowing high reliability for our SOC. This setup provides continuous operation even in the event of an AZ failure, ensuring that our automated workflows are always available.
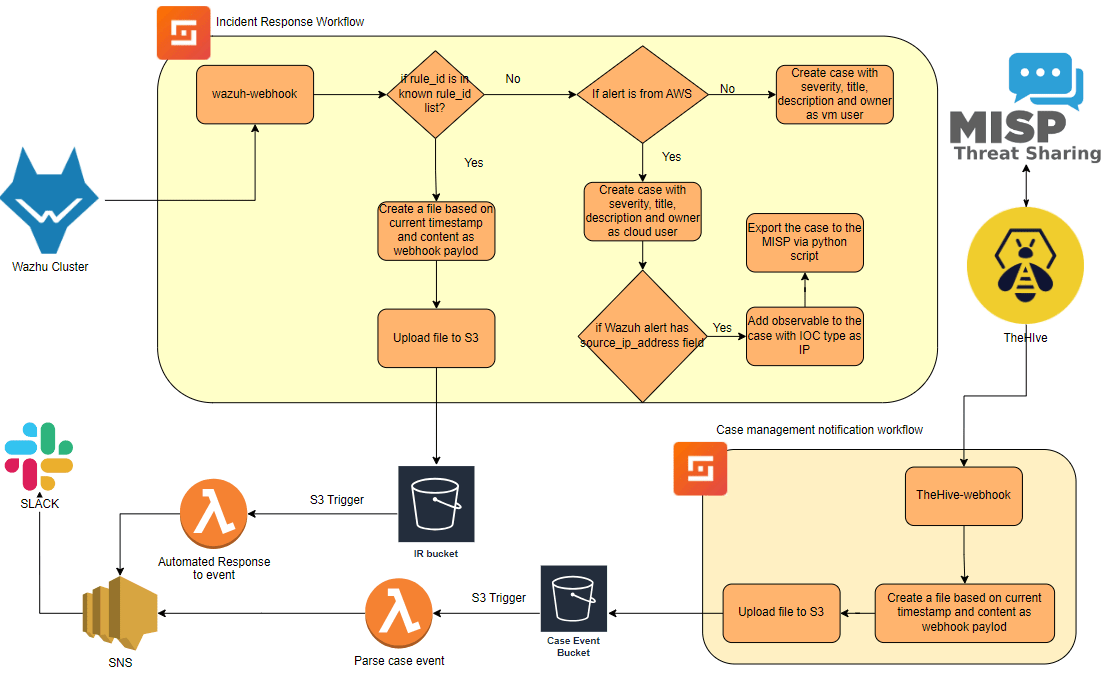
2. Incident Response Workflow
This workflow is designed to automate the response to alerts generated by Wazuh either by creating cases or triggering incident response automation workflows.
The process is as follows:
Triggering the Workflow:The workflow is triggered via a webhook when a Wazuh alert is received. Depending on the rule_id in the alert, the workflow determines the next steps.
Branch Condition Based on Known rule_id:
If the rule_id is in the known list, indicating predefined rules for automated responses:
Upon completion, the status is published via SNS to notify the appropriate team
If the rule_id is not in the known list:
Rule-level mapping:
3. Case Management Notification workflow:
This workflow handles notifications for case creation and closure events in TheHive, ensuring real-time communication with the SOC team.
Here’s how it operates:
The event data is copied to a file and uploaded to an S3 bucket.
The S3 bucket has a Lambda function triggered by object creation events. The function parses the event and generates the appropriate message.
The message is then published to Slack or Email via SNS, notifying the SOC team of case changes in real-time.
In this blog, we have discussed how integrating SOAR platforms like Shuffle into Security Operations Centers (SOCs) significantly enhances their efficiency and effectiveness. As a key solution offered by a cloud services provider in India, Shuffle’s capabilities in creating customizable workflows, seamlessly integrating with various security tools, and automating incident response processes make it indispensable for modern cybersecurity operations. This orchestration and automation reduce manual intervention, ensuring incidents are promptly addressed with accurate and actionable intelligence, thereby strengthening cloud consulting services for improved cloud governance and security.
In our next blog, we will explore how to visualize SOC data to derive meaningful insights. Stay tuned for more on optimizing your SOC operations and enhancing your organization’s security strategy.
CloudifyOps Pvt Ltd, Ground Floor, Block C, DSR Techno Cube, Survey No.68, Varthur Rd, Thubarahalli, Bengaluru, Karnataka 560066
CloudifyOps Pvt Ltd, Cove Offices OMR, 10th Floor, Prince Infocity 1, Old Mahabalipuram Road, 50,1st Street, Kandhanchavadi, Perungudi, Chennai, Tamil Nadu - 600096
CloudifyOps Inc.,
200, Continental Dr Suite 401,
Newark, Delaware 19713,
United States of America
Copyright 2025 CloudifyOps. All Rights Reserved
